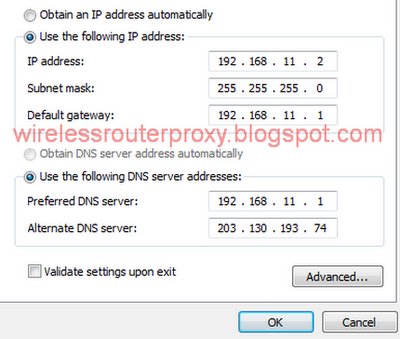
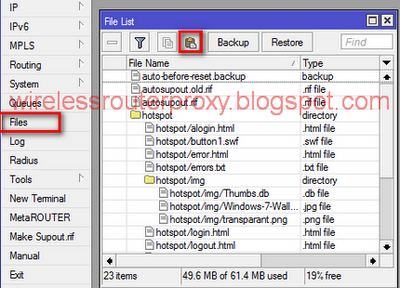
Saturday, December 29, 2012
Wednesday, December 26, 2012
2XWAN
/ip address
add address=192.168.1.3/24 network=192.168.1.0 broadcast=192.168.1.255 interface=WAN1 comment="" disabled=no
add address=192.168.2.3/24 network=192.168.2.0 broadcast=192.168.2.255 interface=WAN2 comment="" disabled=no
add address=10.10.0.1/24 network=10.10.0.0 broadcast=10.10.0.255 interface=internal comment="" disabled=no
/ip firewall mangle
add chain=prerouting in-interface=internal connection-state=new nth=2,1 action=mark-connection new-connection-mark=conn1 passthrough=yes comment="" disabled=no
add chain=prerouting in-interface=internal connection-mark=conn1 action=mark-routing new-routing-mark=conn1 passthrough=no comment="" disabled=no
add chain=prerouting in-interface=internal connection-state=new nth=1,1 action=mark-connection new-connection-mark=conn2 passthrough=yes comment="" disabled=no
add chain=prerouting in-interface=internal connection-mark=conn2 action=mark-routing new-routing-mark=conn2 passthrough=no comment="" disabled=no
/ip firewall nat
add chain=srcnat connection-mark=conn1 action=masquerade out-interface=WAN1 comment="" disabled=no
add chain=srcnat connection-mark=conn2 action=masquerade out-interface=WAN2 comment="" disabled=no
/ip route
add dst-address=0.0.0.0/0 gateway=192.168.1.1 scope=255 target-scope=10 routing-mark=conn1 comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=192.168.2.1 scope=255 target-scope=10 routing-mark=conn2 comment="" disabled=no
add address=192.168.1.3/24 network=192.168.1.0 broadcast=192.168.1.255 interface=WAN1 comment="" disabled=no
add address=192.168.2.3/24 network=192.168.2.0 broadcast=192.168.2.255 interface=WAN2 comment="" disabled=no
add address=10.10.0.1/24 network=10.10.0.0 broadcast=10.10.0.255 interface=internal comment="" disabled=no
/ip firewall mangle
add chain=prerouting in-interface=internal connection-state=new nth=2,1 action=mark-connection new-connection-mark=conn1 passthrough=yes comment="" disabled=no
add chain=prerouting in-interface=internal connection-mark=conn1 action=mark-routing new-routing-mark=conn1 passthrough=no comment="" disabled=no
add chain=prerouting in-interface=internal connection-state=new nth=1,1 action=mark-connection new-connection-mark=conn2 passthrough=yes comment="" disabled=no
add chain=prerouting in-interface=internal connection-mark=conn2 action=mark-routing new-routing-mark=conn2 passthrough=no comment="" disabled=no
/ip firewall nat
add chain=srcnat connection-mark=conn1 action=masquerade out-interface=WAN1 comment="" disabled=no
add chain=srcnat connection-mark=conn2 action=masquerade out-interface=WAN2 comment="" disabled=no
/ip route
add dst-address=0.0.0.0/0 gateway=192.168.1.1 scope=255 target-scope=10 routing-mark=conn1 comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=192.168.2.1 scope=255 target-scope=10 routing-mark=conn2 comment="" disabled=no
4xWAN Load Balanecing
/ip address
add address=10.10.0.1/16 broadcast=10.10.0.255 comment="" disabled=no interface=internet network=10.10.0.0
add address=192.168.1.2/24 broadcast=192.168.1.255 comment="" disabled=no interface=WAN1 network=192.168.1.0
add address=192.168.2.2/24 broadcast=192.168.2.255 comment="" disabled=no interface=WAN2 network=192.168.2.0
add address=192.168.3.2/24 broadcast=192.168.3.255 comment="" disabled=no interface=WAN3 network=192.168.3.0
add address=192.168.4.2/24 broadcast=192.168.4.255 comment="" disabled=no interface=WAN4 network=192.168.4.0
/ip firewall mangle
add action=mark-connection chain=input comment="" disabled=no in-interface=WAN1 new-connection-mark=WAN1_conn passthrough=yes
add action=mark-connection chain=input comment="" disabled=no in-interface=WAN2 new-connection-mark=WAN2_conn passthrough=yes
add action=mark-connection chain=input comment="" disabled=no in-interface=WAN3 new-connection-mark=WAN3_conn passthrough=yes
add action=mark-connection chain=input comment="" disabled=no in-interface=WAN4 new-connection-mark=WAN4_conn passthrough=yes
add action=mark-routing chain=output comment="" connection-mark=WAN1_conn disabled=no new-routing-mark=to_WAN1 passthrough=yes
add action=mark-routing chain=output comment="" connection-mark=WAN2_conn disabled=no new-routing-mark=to_WAN2 passthrough=yes
add action=mark-routing chain=output comment="" connection-mark=WAN3_conn disabled=no new-routing-mark=to_WAN3 passthrough=yes
add action=mark-routing chain=output comment="" connection-mark=WAN4_conn disabled=no new-routing-mark=to_WAN4 passthrough=yes
add action=accept chain=prerouting comment="" disabled=no dst-address=192.168.1.0/24
add action=accept chain=prerouting comment="" disabled=no dst-address=192.168.2.0/24
add action=accept chain=prerouting comment="" disabled=no dst-address=192.168.3.0/24
add action=accept chain=prerouting comment="" disabled=no dst-address=192.168.4.0/24
add action=mark-connection chain=prerouting comment="" disabled=no dst-address-type=!local new-connection-mark=WAN1_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:4/0 src-address=10.0.0.1-10.0.0.255
add action=mark-connection chain=prerouting comment="" disabled=no dst-address-type=!local new-connection-mark=WAN2_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:4/1 src-address=10.0.0.1-10.0.0.255
add action=mark-connection chain=prerouting comment="" disabled=no dst-address-type=!local new-connection-mark=WAN3_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:4/2 src-address=10.0.0.1-10.0.0.255
add action=mark-connection chain=prerouting comment="" disabled=no dst-address-type=!local new-connection-mark=WAN4_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:4/3 src-address=10.0.0.1-10.0.0.255
add action=mark-routing chain=prerouting comment="" connection-mark=WAN1_conn disabled=no new-routing-mark=to_WAN1 passthrough=yes
add action=mark-routing chain=prerouting comment="" connection-mark=WAN2_conn disabled=no new-routing-mark=to_WAN2 passthrough=yes
add action=mark-routing chain=prerouting comment="" connection-mark=WAN3_conn disabled=no new-routing-mark=to_WAN3 passthrough=yes
add action=mark-routing chain=prerouting comment="" connection-mark=WAN4_conn disabled=no new-routing-mark=to_WAN4 passthrough=yes
/ip firewall nat
add action=masquerade chain=srcnat comment="" disabled=no out-interface=WAN1 src-address=10.0.0.1-10.0.0.255
add action=masquerade chain=srcnat comment="" disabled=no out-interface=WAN2 src-address=10.0.0.1-10.0.0.255
add action=masquerade chain=srcnat comment="" disabled=no out-interface=WAN3 src-address=10.0.0.1-10.0.0.255
add action=masquerade chain=srcnat comment="" disabled=no out-interface=WAN4 src-address=10.0.0.1-10.0.0.255
/ip route
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.1.1 routing-mark=to_WAN1 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.2.1 routing-mark=to_WAN2 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.3.1 routing-mark=to_WAN3 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.4.1 routing-mark=to_WAN4 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.1.1 scope=30 target-scope=10
add check-gateway=ping comment="" disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.2.1 scope=30 target-scope=10
add check-gateway=ping comment="" disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.3.1 scope=30 target-scope=10
add check-gateway=ping comment="" disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.4.1 scope=30 target-scope=10
add address=10.10.0.1/16 broadcast=10.10.0.255 comment="" disabled=no interface=internet network=10.10.0.0
add address=192.168.1.2/24 broadcast=192.168.1.255 comment="" disabled=no interface=WAN1 network=192.168.1.0
add address=192.168.2.2/24 broadcast=192.168.2.255 comment="" disabled=no interface=WAN2 network=192.168.2.0
add address=192.168.3.2/24 broadcast=192.168.3.255 comment="" disabled=no interface=WAN3 network=192.168.3.0
add address=192.168.4.2/24 broadcast=192.168.4.255 comment="" disabled=no interface=WAN4 network=192.168.4.0
/ip firewall mangle
add action=mark-connection chain=input comment="" disabled=no in-interface=WAN1 new-connection-mark=WAN1_conn passthrough=yes
add action=mark-connection chain=input comment="" disabled=no in-interface=WAN2 new-connection-mark=WAN2_conn passthrough=yes
add action=mark-connection chain=input comment="" disabled=no in-interface=WAN3 new-connection-mark=WAN3_conn passthrough=yes
add action=mark-connection chain=input comment="" disabled=no in-interface=WAN4 new-connection-mark=WAN4_conn passthrough=yes
add action=mark-routing chain=output comment="" connection-mark=WAN1_conn disabled=no new-routing-mark=to_WAN1 passthrough=yes
add action=mark-routing chain=output comment="" connection-mark=WAN2_conn disabled=no new-routing-mark=to_WAN2 passthrough=yes
add action=mark-routing chain=output comment="" connection-mark=WAN3_conn disabled=no new-routing-mark=to_WAN3 passthrough=yes
add action=mark-routing chain=output comment="" connection-mark=WAN4_conn disabled=no new-routing-mark=to_WAN4 passthrough=yes
add action=accept chain=prerouting comment="" disabled=no dst-address=192.168.1.0/24
add action=accept chain=prerouting comment="" disabled=no dst-address=192.168.2.0/24
add action=accept chain=prerouting comment="" disabled=no dst-address=192.168.3.0/24
add action=accept chain=prerouting comment="" disabled=no dst-address=192.168.4.0/24
add action=mark-connection chain=prerouting comment="" disabled=no dst-address-type=!local new-connection-mark=WAN1_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:4/0 src-address=10.0.0.1-10.0.0.255
add action=mark-connection chain=prerouting comment="" disabled=no dst-address-type=!local new-connection-mark=WAN2_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:4/1 src-address=10.0.0.1-10.0.0.255
add action=mark-connection chain=prerouting comment="" disabled=no dst-address-type=!local new-connection-mark=WAN3_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:4/2 src-address=10.0.0.1-10.0.0.255
add action=mark-connection chain=prerouting comment="" disabled=no dst-address-type=!local new-connection-mark=WAN4_conn passthrough=yes per-connection-classifier=both-addresses-and-ports:4/3 src-address=10.0.0.1-10.0.0.255
add action=mark-routing chain=prerouting comment="" connection-mark=WAN1_conn disabled=no new-routing-mark=to_WAN1 passthrough=yes
add action=mark-routing chain=prerouting comment="" connection-mark=WAN2_conn disabled=no new-routing-mark=to_WAN2 passthrough=yes
add action=mark-routing chain=prerouting comment="" connection-mark=WAN3_conn disabled=no new-routing-mark=to_WAN3 passthrough=yes
add action=mark-routing chain=prerouting comment="" connection-mark=WAN4_conn disabled=no new-routing-mark=to_WAN4 passthrough=yes
/ip firewall nat
add action=masquerade chain=srcnat comment="" disabled=no out-interface=WAN1 src-address=10.0.0.1-10.0.0.255
add action=masquerade chain=srcnat comment="" disabled=no out-interface=WAN2 src-address=10.0.0.1-10.0.0.255
add action=masquerade chain=srcnat comment="" disabled=no out-interface=WAN3 src-address=10.0.0.1-10.0.0.255
add action=masquerade chain=srcnat comment="" disabled=no out-interface=WAN4 src-address=10.0.0.1-10.0.0.255
/ip route
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.1.1 routing-mark=to_WAN1 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.2.1 routing-mark=to_WAN2 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.3.1 routing-mark=to_WAN3 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.4.1 routing-mark=to_WAN4 scope=30 target-scope=10
add check-gateway=ping disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.1.1 scope=30 target-scope=10
add check-gateway=ping comment="" disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.2.1 scope=30 target-scope=10
add check-gateway=ping comment="" disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.3.1 scope=30 target-scope=10
add check-gateway=ping comment="" disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.4.1 scope=30 target-scope=10
Nginx RB
#!/usr/bin/env ruby1.8
# This script is not written by me,
# My Email address is inserted Just for tracking purposes
# For more info, visit http://code.google.com/p/youtube-cache/
# Syed Jahanzaib / aacable [at] hotmail.com
# url_rewrite_program/nginx.rb
# url_rewrite_host_header off
require "syslog"
require "base64"
class SquidRequest
attr_accessor :url, :user
attr_reader :client_ip, :method
def method=(s)
@method = s.downcase
end
def client_ip=(s)
@client_ip = s.split('/').first
end
end
def read_requests
# URL client_ip "/" fqdn user method [ kvpairs]
STDIN.each_line do |ln|
r = SquidRequest.new
r.url, r.client_ip, r.user, r.method, *dummy = ln.rstrip.split(' ')
(STDOUT << "#{yield r}\n").flush
end
end
def log(msg)
Syslog.log(Syslog::LOG_ERR, "%s", msg)
end
def main
Syslog.open('nginx.rb', Syslog::LOG_PID)
log("Started")
read_requests do |r|
if r.method == 'get' && r.url !~ /[?&]begin=/ && r.url =~ %r{\Ahttp://[^/]+\.youtube\.com/(videoplayback\?.*)\z}
log("YouTube Video [#{r.url}].")
"http://127.0.0.1:8081/#{$1}"
else
r.url
end
end
end
main
# This script is not written by me,
# My Email address is inserted Just for tracking purposes
# For more info, visit http://code.google.com/p/youtube-cache/
# Syed Jahanzaib / aacable [at] hotmail.com
# url_rewrite_program
# url_rewrite_host_header off
require "syslog"
require "base64"
class SquidRequest
attr_accessor :url, :user
attr_reader :client_ip, :method
def method=(s)
@method = s.downcase
end
def client_ip=(s)
@client_ip = s.split('/').first
end
end
def read_requests
# URL
STDIN.each_line do |ln|
r = SquidRequest.new
r.url, r.client_ip, r.user, r.method, *dummy = ln.rstrip.split(' ')
(STDOUT << "#{yield r}\n").flush
end
end
def log(msg)
Syslog.log(Syslog::LOG_ERR, "%s", msg)
end
def main
Syslog.open('nginx.rb', Syslog::LOG_PID)
log("Started")
read_requests do |r|
if r.method == 'get' && r.url !~ /[?&]begin=/ && r.url =~ %r{\Ahttp://[^/]+\.youtube\.com/(videoplayback\?.*)\z}
log("YouTube Video [#{r.url}].")
"http://127.0.0.1:8081/#{$1}"
else
r.url
end
end
end
main
Store URL
#!/usr/bin/perl
# This script is NOT written or modified by me, I only copy pasted it from the internet.
# It was First originally Writen by chudy_fernandez@yahoo.com
# & Have been modified by various persons over the net to fix/add various functions.
# Like For Example modified by member of comstuff.net to satisfy common and dynamic content.
# th30nly @comstuff.net a.k.a invisible_theater , and possibly other people too.
# For more info, http://wiki.squid-cache.org/ConfigExamples/DynamicContent/YouTube
# Adeel Ahmed / adeelkml1 @ gmail . com
$|=1;
while (<>) {
@X = split;
# $X[1] =~ s/&sig=.*//;
$x = $X[0] . " ";
$_ = $X[1];
$u = $X[1];
if ($X[1] =~ /(youtube|google).*videoplayback\?/){
@itag = m/[&?](itag=[0-9]*)/;
@id = m/[&?](id=[^\&]*)/;
@range = m/[&?](range=[^\&\s]*)/;
@begin = m/[&?](begin=[^\&\s]*)/;
@redirect = m/[&?](redirect_counter=[^\&]*)/;
print $x . "http://video-srv.youtube.com.SQUIDINTERNAL/@itag&@id&@range@begin@redirect\n";
#speedtest
}elsif (m/^http:\/\/(.*)\/speedtest\/(.*\.(jpg|txt))\?(.*)/) {
print $x . "http://www.speedtest.net.SQUIDINTERNAL/speedtest/" . $2 . "\n";
#mediafire
}elsif (m/^http:\/\/199\.91\.15\d\.\d*\/\w{12}\/(\w*)\/(.*)/) {
print $x . "http://www.mediafire.com.SQUIDINTERNAL/" . $1 ."/" . $2 . "\n";
#fileserve
}elsif (m/^http:\/\/fs\w*\.fileserve\.com\/file\/(\w*)\/[\w-]*\.\/(.*)/) {
print $x . "http://www.fileserve.com.SQUIDINTERNAL/" . $1 . "./" . $2 . "\n";
#filesonic
}elsif (m/^http:\/\/s[0-9]*\.filesonic\.com\/download\/([0-9]*)\/(.*)/) {
print $x . "http://www.filesonic.com.SQUIDINTERNAL/" . $1 . "\n";
#4shared
}elsif (m/^http:\/\/[a-zA-Z]{2}\d*\.4shared\.com(:8080|)\/download\/(.*)\/(.*\..*)\?.*/) {
print $x . "http://www.4shared.com.SQUIDINTERNAL/download/$2\/$3\n";
#4shared preview
}elsif (m/^http:\/\/[a-zA-Z]{2}\d*\.4shared\.com(:8080|)\/img\/(\d*)\/\w*\/dlink__2Fdownload_2F(\w*)_3Ftsid_3D[\w-]*\/preview\.mp3\?sId=\w*/) {
print $x . "http://www.4shared.com.SQUIDINTERNAL/$2\n";
#photos-X.ak.fbcdn.net where X a-z
}elsif (m/^http:\/\/photos-[a-z](\.ak\.fbcdn\.net)(\/.*\/)(.*\.jpg)/) {
print $x . "http://photos" . $1 . "/" . $2 . $3 . "\n";
#YX.sphotos.ak.fbcdn.net where X 1-9, Y a-z
} elsif (m/^http:\/\/[a-z][0-9]\.sphotos\.ak\.fbcdn\.net\/(.*)\/(.*)/) {
print $x . "http://photos.ak.fbcdn.net/" . $1 ."/". $2 . "\n";
#maps.google.com
} elsif (m/^http:\/\/(cbk|mt|khm|mlt|tbn)[0-9]?(.google\.co(m|\.uk|\.id).*)/) {
print $x . "http://" . $1 . $2 . "\n";
# compatibility for old cached get_video?video_id
} elsif (m/^http:\/\/([0-9.]{4}|.*\.youtube\.com|.*\.googlevideo\.com|.*\.video\.google\.com).*?(videoplayback\?id=.*?|video_id=.*?)\&(.*?)/) {
$z = $2; $z =~ s/video_id=/get_video?video_id=/;
print $x . "http://video-srv.youtube.com.SQUIDINTERNAL/" . $z . "\n";
} elsif (m/^http:\/\/www\.google-analytics\.com\/__utm\.gif\?.*/) {
print $x . "http://www.google-analytics.com/__utm.gif\n";
#Cache High Latency Ads
} elsif (m/^http:\/\/([a-z0-9.]*)(\.doubleclick\.net|\.quantserve\.com|\.googlesyndication\.com|yieldmanager|cpxinteractive)(.*)/) {
$y = $3;$z = $2;
for ($y) {
s/pixel;.*/pixel/;
s/activity;.*/activity/;
s/(imgad[^&]*).*/\1/;
s/;ord=[?0-9]*//;
s/;×tamp=[0-9]*//;
s/[&?]correlator=[0-9]*//;
s/&cookie=[^&]*//;
s/&ga_hid=[^&]*//;
s/&ga_vid=[^&]*//;
s/&ga_sid=[^&]*//;
# s/&prev_slotnames=[^&]*//
# s/&u_his=[^&]*//;
s/&dt=[^&]*//;
s/&dtd=[^&]*//;
s/&lmt=[^&]*//;
s/(&alternate_ad_url=http%3A%2F%2F[^(%2F)]*)[^&]*/\1/;
s/(&url=http%3A%2F%2F[^(%2F)]*)[^&]*/\1/;
s/(&ref=http%3A%2F%2F[^(%2F)]*)[^&]*/\1/;
s/(&cookie=http%3A%2F%2F[^(%2F)]*)[^&]*/\1/;
s/[;&?]ord=[?0-9]*//;
s/[;&]mpvid=[^&;]*//;
s/&xpc=[^&]*//;
# yieldmanager
s/\?clickTag=[^&]*//;
s/&u=[^&]*//;
s/&slotname=[^&]*//;
s/&page_slots=[^&]*//;
}
print $x . "http://" . $1 . $2 . $y . "\n";
#cache high latency ads
} elsif (m/^http:\/\/(.*?)\/(ads)\?(.*?)/) {
print $x . "http://" . $1 . "/" . $2 . "\n";
# spicific servers starts here....
} elsif (m/^http:\/\/(www\.ziddu\.com.*\.[^\/]{3,4})\/(.*?)/) {
print $x . "http://" . $1 . "\n";
#cdn, varialble 1st path
} elsif (($u =~ /filehippo/) && (m/^http:\/\/(.*?)\.(.*?)\/(.*?)\/(.*)\.([a-z0-9]{3,4})(\?.*)?/)) {
@y = ($1,$2,$4,$5);
$y[0] =~ s/[a-z0-9]{2,5}/cdn./;
print $x . "http://" . $y[0] . $y[1] . "/" . $y[2] . "." . $y[3] . "\n";
#rapidshare
} elsif (($u =~ /rapidshare/) && (m/^http:\/\/(([A-Za-z]+[0-9-.]+)*?)([a-z]*\.[^\/]{3}\/[a-z]*\/[0-9]*)\/(.*?)\/([^\/\?\&]{4,})$/)) {
print $x . "http://cdn." . $3 . "/SQUIDINTERNAL/" . $5 . "\n";
} elsif (($u =~ /maxporn/) && (m/^http:\/\/([^\/]*?)\/(.*?)\/([^\/]*?)(\?.*)?$/)) {
print $x . "http://" . $1 . "/SQUIDINTERNAL/" . $3 . "\n";
#like porn hub variables url and center part of the path, filename etention 3 or 4 with or without ? at the end
} elsif (($u =~ /tube8|pornhub|xvideos/) && (m/^http:\/\/(([A-Za-z]+[0-9-.]+)*?(\.[a-z]*)?)\.([a-z]*[0-9]?\.[^\/]{3}\/[a-z]*)(.*?)((\/[a-z]*)?(\/[^\/]*){4}\.[^\/\?]{3,4})(\?.*)?$/)) {
print $x . "http://cdn." . $4 . $6 . "\n";
#...spicific servers end here.
#photos-X.ak.fbcdn.net where X a-z
} elsif (m/^http:\/\/photos-[a-z].ak.fbcdn.net\/(.*)/) {
print $x . "http://photos.ak.fbcdn.net/" . $1 . "\n";
#for yimg.com video
} elsif (m/^http:\/\/(.*yimg.com)\/\/(.*)\/([^\/\?\&]*\/[^\/\?\&]*\.[^\/\?\&]{3,4})(\?.*)?$/) {
print $x . "http://cdn.yimg.com//" . $3 . "\n";
#for yimg.com doubled
} elsif (m/^http:\/\/(.*?)\.yimg\.com\/(.*?)\.yimg\.com\/(.*?)\?(.*)/) {
print $x . "http://cdn.yimg.com/" . $3 . "\n";
#for yimg.com with &sig=
} elsif (m/^http:\/\/(.*?)\.yimg\.com\/(.*)/) {
@y = ($1,$2);
$y[0] =~ s/[a-z]+[0-9]+/cdn/;
$y[1] =~ s/&sig=.*//;
print $x . "http://" . $y[0] . ".yimg.com/" . $y[1] . "\n";
#youjizz. We use only domain and filename
} elsif (($u =~ /media[0-9]{2,5}\.youjizz/) && (m/^http:\/\/(.*)(\.[^\.\-]*?\..*?)\/(.*)\/([^\/\?\&]*)\.([^\/\?\&]{3,4})((\?|\%).*)?$/)) {
@y = ($1,$2,$4,$5);
$y[0] =~ s/(([a-zA-A]+[0-9]+(-[a-zA-Z])?$)|(.*cdn.*)|(.*cache.*))/cdn/;
print $x . "http://" . $y[0] . $y[1] . "/" . $y[2] . "." . $y[3] . "\n";
#general purpose for cdn servers. add above your specific servers.
} elsif (m/^http:\/\/([0-9.]*?)\/\/(.*?)\.(.*)\?(.*?)/) {
print $x . "http://squid-cdn-url//" . $2 . "." . $3 . "\n";
#generic http://variable.domain.com/path/filename."ex" "ext" or "exte" with or withour "? or %"
} elsif (m/^http:\/\/(.*)(\.[^\.\-]*?\..*?)\/(.*)\.([^\/\?\&]{2,4})((\?|\%).*)?$/) {
@y = ($1,$2,$3,$4);
$y[0] =~ s/(([a-zA-A]+[0-9]+(-[a-zA-Z])?$)|(.*cdn.*)|(.*cache.*))/cdn/;
print $x . "http://" . $y[0] . $y[1] . "/" . $y[2] . "." . $y[3] . "\n";
# generic http://variable.domain.com/...
} elsif (m/^http:\/\/(([A-Za-z]+[0-9-]+)*?|.*cdn.*|.*cache.*)\.(.*?)\.(.*?)\/(.*)$/) {
print $x . "http://cdn." . $3 . "." . $4 . "/" . $5 . "\n";
# spicific extention that ends with ?
} elsif (m/^http:\/\/(.*?)\/(.*?)\.(jp(e?g|e|2)|gif|png|tiff?|bmp|ico|flv|wmv|3gp|mp(4|3)|exe|msi|zip|on2|mar|rar|cab|amf|swf)(.*)/) {
print $x . "http://" . $1 . "/" . $2 . "." . $3 . "\n";
# all that ends with ;
} elsif (m/^http:\/\/(.*?)\/(.*?)\;(.*)/) {
print $x . "http://" . $1 . "/" . $2 . "\n";
} else {
print $x . $_ . "sucks\n";
}
}
# This script is NOT written or modified by me, I only copy pasted it from the internet.
# It was First originally Writen by chudy_fernandez@yahoo.com
# & Have been modified by various persons over the net to fix/add various functions.
# Like For Example modified by member of comstuff.net to satisfy common and dynamic content.
# th30nly @comstuff.net a.k.a invisible_theater , and possibly other people too.
# For more info, http://wiki.squid-cache.org/ConfigExamples/DynamicContent/YouTube
# Adeel Ahmed / adeelkml1 @ gmail . com
$|=1;
while (<>) {
@X = split;
# $X[1] =~ s/&sig=.*//;
$x = $X[0] . " ";
$_ = $X[1];
$u = $X[1];
if ($X[1] =~ /(youtube|google).*videoplayback\?/){
@itag = m/[&?](itag=[0-9]*)/;
@id = m/[&?](id=[^\&]*)/;
@range = m/[&?](range=[^\&\s]*)/;
@begin = m/[&?](begin=[^\&\s]*)/;
@redirect = m/[&?](redirect_counter=[^\&]*)/;
print $x . "http://video-srv.youtube.com.SQUIDINTERNAL/@itag&@id&@range@begin@redirect\n";
#speedtest
}elsif (m/^http:\/\/(.*)\/speedtest\/(.*\.(jpg|txt))\?(.*)/) {
print $x . "http://www.speedtest.net.SQUIDINTERNAL/speedtest/" . $2 . "\n";
#mediafire
}elsif (m/^http:\/\/199\.91\.15\d\.\d*\/\w{12}\/(\w*)\/(.*)/) {
print $x . "http://www.mediafire.com.SQUIDINTERNAL/" . $1 ."/" . $2 . "\n";
#fileserve
}elsif (m/^http:\/\/fs\w*\.fileserve\.com\/file\/(\w*)\/[\w-]*\.\/(.*)/) {
print $x . "http://www.fileserve.com.SQUIDINTERNAL/" . $1 . "./" . $2 . "\n";
#filesonic
}elsif (m/^http:\/\/s[0-9]*\.filesonic\.com\/download\/([0-9]*)\/(.*)/) {
print $x . "http://www.filesonic.com.SQUIDINTERNAL/" . $1 . "\n";
#4shared
}elsif (m/^http:\/\/[a-zA-Z]{2}\d*\.4shared\.com(:8080|)\/download\/(.*)\/(.*\..*)\?.*/) {
print $x . "http://www.4shared.com.SQUIDINTERNAL/download/$2\/$3\n";
#4shared preview
}elsif (m/^http:\/\/[a-zA-Z]{2}\d*\.4shared\.com(:8080|)\/img\/(\d*)\/\w*\/dlink__2Fdownload_2F(\w*)_3Ftsid_3D[\w-]*\/preview\.mp3\?sId=\w*/) {
print $x . "http://www.4shared.com.SQUIDINTERNAL/$2\n";
#photos-X.ak.fbcdn.net where X a-z
}elsif (m/^http:\/\/photos-[a-z](\.ak\.fbcdn\.net)(\/.*\/)(.*\.jpg)/) {
print $x . "http://photos" . $1 . "/" . $2 . $3 . "\n";
#YX.sphotos.ak.fbcdn.net where X 1-9, Y a-z
} elsif (m/^http:\/\/[a-z][0-9]\.sphotos\.ak\.fbcdn\.net\/(.*)\/(.*)/) {
print $x . "http://photos.ak.fbcdn.net/" . $1 ."/". $2 . "\n";
#maps.google.com
} elsif (m/^http:\/\/(cbk|mt|khm|mlt|tbn)[0-9]?(.google\.co(m|\.uk|\.id).*)/) {
print $x . "http://" . $1 . $2 . "\n";
# compatibility for old cached get_video?video_id
} elsif (m/^http:\/\/([0-9.]{4}|.*\.youtube\.com|.*\.googlevideo\.com|.*\.video\.google\.com).*?(videoplayback\?id=.*?|video_id=.*?)\&(.*?)/) {
$z = $2; $z =~ s/video_id=/get_video?video_id=/;
print $x . "http://video-srv.youtube.com.SQUIDINTERNAL/" . $z . "\n";
} elsif (m/^http:\/\/www\.google-analytics\.com\/__utm\.gif\?.*/) {
print $x . "http://www.google-analytics.com/__utm.gif\n";
#Cache High Latency Ads
} elsif (m/^http:\/\/([a-z0-9.]*)(\.doubleclick\.net|\.quantserve\.com|\.googlesyndication\.com|yieldmanager|cpxinteractive)(.*)/) {
$y = $3;$z = $2;
for ($y) {
s/pixel;.*/pixel/;
s/activity;.*/activity/;
s/(imgad[^&]*).*/\1/;
s/;ord=[?0-9]*//;
s/;×tamp=[0-9]*//;
s/[&?]correlator=[0-9]*//;
s/&cookie=[^&]*//;
s/&ga_hid=[^&]*//;
s/&ga_vid=[^&]*//;
s/&ga_sid=[^&]*//;
# s/&prev_slotnames=[^&]*//
# s/&u_his=[^&]*//;
s/&dt=[^&]*//;
s/&dtd=[^&]*//;
s/&lmt=[^&]*//;
s/(&alternate_ad_url=http%3A%2F%2F[^(%2F)]*)[^&]*/\1/;
s/(&url=http%3A%2F%2F[^(%2F)]*)[^&]*/\1/;
s/(&ref=http%3A%2F%2F[^(%2F)]*)[^&]*/\1/;
s/(&cookie=http%3A%2F%2F[^(%2F)]*)[^&]*/\1/;
s/[;&?]ord=[?0-9]*//;
s/[;&]mpvid=[^&;]*//;
s/&xpc=[^&]*//;
# yieldmanager
s/\?clickTag=[^&]*//;
s/&u=[^&]*//;
s/&slotname=[^&]*//;
s/&page_slots=[^&]*//;
}
print $x . "http://" . $1 . $2 . $y . "\n";
#cache high latency ads
} elsif (m/^http:\/\/(.*?)\/(ads)\?(.*?)/) {
print $x . "http://" . $1 . "/" . $2 . "\n";
# spicific servers starts here....
} elsif (m/^http:\/\/(www\.ziddu\.com.*\.[^\/]{3,4})\/(.*?)/) {
print $x . "http://" . $1 . "\n";
#cdn, varialble 1st path
} elsif (($u =~ /filehippo/) && (m/^http:\/\/(.*?)\.(.*?)\/(.*?)\/(.*)\.([a-z0-9]{3,4})(\?.*)?/)) {
@y = ($1,$2,$4,$5);
$y[0] =~ s/[a-z0-9]{2,5}/cdn./;
print $x . "http://" . $y[0] . $y[1] . "/" . $y[2] . "." . $y[3] . "\n";
#rapidshare
} elsif (($u =~ /rapidshare/) && (m/^http:\/\/(([A-Za-z]+[0-9-.]+)*?)([a-z]*\.[^\/]{3}\/[a-z]*\/[0-9]*)\/(.*?)\/([^\/\?\&]{4,})$/)) {
print $x . "http://cdn." . $3 . "/SQUIDINTERNAL/" . $5 . "\n";
} elsif (($u =~ /maxporn/) && (m/^http:\/\/([^\/]*?)\/(.*?)\/([^\/]*?)(\?.*)?$/)) {
print $x . "http://" . $1 . "/SQUIDINTERNAL/" . $3 . "\n";
#like porn hub variables url and center part of the path, filename etention 3 or 4 with or without ? at the end
} elsif (($u =~ /tube8|pornhub|xvideos/) && (m/^http:\/\/(([A-Za-z]+[0-9-.]+)*?(\.[a-z]*)?)\.([a-z]*[0-9]?\.[^\/]{3}\/[a-z]*)(.*?)((\/[a-z]*)?(\/[^\/]*){4}\.[^\/\?]{3,4})(\?.*)?$/)) {
print $x . "http://cdn." . $4 . $6 . "\n";
#...spicific servers end here.
#photos-X.ak.fbcdn.net where X a-z
} elsif (m/^http:\/\/photos-[a-z].ak.fbcdn.net\/(.*)/) {
print $x . "http://photos.ak.fbcdn.net/" . $1 . "\n";
#for yimg.com video
} elsif (m/^http:\/\/(.*yimg.com)\/\/(.*)\/([^\/\?\&]*\/[^\/\?\&]*\.[^\/\?\&]{3,4})(\?.*)?$/) {
print $x . "http://cdn.yimg.com//" . $3 . "\n";
#for yimg.com doubled
} elsif (m/^http:\/\/(.*?)\.yimg\.com\/(.*?)\.yimg\.com\/(.*?)\?(.*)/) {
print $x . "http://cdn.yimg.com/" . $3 . "\n";
#for yimg.com with &sig=
} elsif (m/^http:\/\/(.*?)\.yimg\.com\/(.*)/) {
@y = ($1,$2);
$y[0] =~ s/[a-z]+[0-9]+/cdn/;
$y[1] =~ s/&sig=.*//;
print $x . "http://" . $y[0] . ".yimg.com/" . $y[1] . "\n";
#youjizz. We use only domain and filename
} elsif (($u =~ /media[0-9]{2,5}\.youjizz/) && (m/^http:\/\/(.*)(\.[^\.\-]*?\..*?)\/(.*)\/([^\/\?\&]*)\.([^\/\?\&]{3,4})((\?|\%).*)?$/)) {
@y = ($1,$2,$4,$5);
$y[0] =~ s/(([a-zA-A]+[0-9]+(-[a-zA-Z])?$)|(.*cdn.*)|(.*cache.*))/cdn/;
print $x . "http://" . $y[0] . $y[1] . "/" . $y[2] . "." . $y[3] . "\n";
#general purpose for cdn servers. add above your specific servers.
} elsif (m/^http:\/\/([0-9.]*?)\/\/(.*?)\.(.*)\?(.*?)/) {
print $x . "http://squid-cdn-url//" . $2 . "." . $3 . "\n";
#generic http://variable.domain.com/path/filename."ex" "ext" or "exte" with or withour "? or %"
} elsif (m/^http:\/\/(.*)(\.[^\.\-]*?\..*?)\/(.*)\.([^\/\?\&]{2,4})((\?|\%).*)?$/) {
@y = ($1,$2,$3,$4);
$y[0] =~ s/(([a-zA-A]+[0-9]+(-[a-zA-Z])?$)|(.*cdn.*)|(.*cache.*))/cdn/;
print $x . "http://" . $y[0] . $y[1] . "/" . $y[2] . "." . $y[3] . "\n";
# generic http://variable.domain.com/...
} elsif (m/^http:\/\/(([A-Za-z]+[0-9-]+)*?|.*cdn.*|.*cache.*)\.(.*?)\.(.*?)\/(.*)$/) {
print $x . "http://cdn." . $3 . "." . $4 . "/" . $5 . "\n";
# spicific extention that ends with ?
} elsif (m/^http:\/\/(.*?)\/(.*?)\.(jp(e?g|e|2)|gif|png|tiff?|bmp|ico|flv|wmv|3gp|mp(4|3)|exe|msi|zip|on2|mar|rar|cab|amf|swf)(.*)/) {
print $x . "http://" . $1 . "/" . $2 . "." . $3 . "\n";
# all that ends with ;
} elsif (m/^http:\/\/(.*?)\/(.*?)\;(.*)/) {
print $x . "http://" . $1 . "/" . $2 . "\n";
} else {
print $x . $_ . "sucks\n";
}
}
Interner Sharing
#!/bin/sh
# ------------------------------------------------------------------------------------
# See URL: http://www.cyberciti.biz/tips/linux-setup-transparent-proxy-squid-howto.html
# (c) 2006, nixCraft under GNU/GPL v2.0+
# http://adeelkml.com
# -------------------------------------------------------------------------------------
## Squid Server LAN IP Address
SQUID_SERVER="192.168.2.1"
## Interface connected to Internet
INTERNET="eth1"
## Interface connected to LAN
LAN_IN="eth0"
## Squid port
SQUID_PORT="8080"
# Clear old firewall
iptables -F
iptables -X
iptables -t nat -F
iptables -t nat -X
iptables -t mangle -F
iptables -t mangle -X
## Load IPTABLES modules for NAT and IP conntrack support
modprobe ip_conntrack
modprobe ip_conntrack_ftp
## For win xp ftp client
## modprobe ip_nat_ftp
echo 1 > /proc/sys/net/ipv4/ip_forward
## Setting default filter policy
## iptables -P INPUT DROP
iptables -P OUTPUT ACCEPT
## Unlimited access to loop back
iptables -A INPUT -i lo -j ACCEPT
iptables -A OUTPUT -o lo -j ACCEPT
## Allow UDP, DNS and Passive FTP
iptables -A INPUT -i $INTERNET -m state --state ESTABLISHED,RELATED -j ACCEPT
## set this system as a router for Rest of LAN
iptables --table nat --append POSTROUTING --out-interface $INTERNET -j MASQUERADE
iptables --append FORWARD --in-interface $LAN_IN -j ACCEPT
## unlimited access to LAN
iptables -A INPUT -i $LAN_IN -j ACCEPT
iptables -A OUTPUT -o $LAN_IN -j ACCEPT
## DNAT port 80 request comming from LAN systems to squid 3128 ($SQUID_PORT) aka transparent proxy
iptables -t nat -A PREROUTING -i $LAN_IN -p tcp --dport 80 -j DNAT --to $SQUID_SERVER:$SQUID_PORT
## if it is same system
iptables -t nat -A PREROUTING -i $INTERNET -p tcp --dport 80 -j REDIRECT --to-port $SQUID_PORT
## LOG everything
iptables -A INPUT -j LOG
## Drop Everything else. I m not enabling it, use it at your own.
##iptables -A INPUT -j DROP
# ------------------------------------------------------------------------------------
# See URL: http://www.cyberciti.biz/tips/linux-setup-transparent-proxy-squid-howto.html
# (c) 2006, nixCraft under GNU/GPL v2.0+
# http://adeelkml.com
# -------------------------------------------------------------------------------------
## Squid Server LAN IP Address
SQUID_SERVER="192.168.2.1"
## Interface connected to Internet
INTERNET="eth1"
## Interface connected to LAN
LAN_IN="eth0"
## Squid port
SQUID_PORT="8080"
# Clear old firewall
iptables -F
iptables -X
iptables -t nat -F
iptables -t nat -X
iptables -t mangle -F
iptables -t mangle -X
## Load IPTABLES modules for NAT and IP conntrack support
modprobe ip_conntrack
modprobe ip_conntrack_ftp
## For win xp ftp client
## modprobe ip_nat_ftp
echo 1 > /proc/sys/net/ipv4/ip_forward
## Setting default filter policy
## iptables -P INPUT DROP
iptables -P OUTPUT ACCEPT
## Unlimited access to loop back
iptables -A INPUT -i lo -j ACCEPT
iptables -A OUTPUT -o lo -j ACCEPT
## Allow UDP, DNS and Passive FTP
iptables -A INPUT -i $INTERNET -m state --state ESTABLISHED,RELATED -j ACCEPT
## set this system as a router for Rest of LAN
iptables --table nat --append POSTROUTING --out-interface $INTERNET -j MASQUERADE
iptables --append FORWARD --in-interface $LAN_IN -j ACCEPT
## unlimited access to LAN
iptables -A INPUT -i $LAN_IN -j ACCEPT
iptables -A OUTPUT -o $LAN_IN -j ACCEPT
## DNAT port 80 request comming from LAN systems to squid 3128 ($SQUID_PORT) aka transparent proxy
iptables -t nat -A PREROUTING -i $LAN_IN -p tcp --dport 80 -j DNAT --to $SQUID_SERVER:$SQUID_PORT
## if it is same system
iptables -t nat -A PREROUTING -i $INTERNET -p tcp --dport 80 -j REDIRECT --to-port $SQUID_PORT
## LOG everything
iptables -A INPUT -j LOG
## Drop Everything else. I m not enabling it, use it at your own.
##iptables -A INPUT -j DROP
Commend for new proxy
Source:isp-tech.net
Credits:Syed Jahanzaib
Note:Copy One Line at a time
1:Create file
touch /etc/fw.sh
2:Change permissions
chmod +x /etc/fw.sh
3:Edit File
nano /etc/fw.sh
(Add the script simple internet sharing)
4:Run
/etc/fw.sh
5:Place shortcut
/etc/rc.local
6:Upgrade DNS
apt-get install dnsmasq
7:Update system
apt-get update
8:Install Squid
apt-get install squid
9:Edit squid.conf
nano /etc/squid/squid.conf
(Add the script squid.conf)
10:create storeurl.pl
touch /etc/squid/storeurl.pl
chmod +x /etc/squid/storeurl.pl
11:Edit store URL
nano /etc/squid/storeurl.pl
(Add store URL Script)
12:Install Nginx
apt-get install nginx
13:Edit Nginx.conf
nano /etc/nginx/nginx.conf
(Delete all lines in Nginx.conf)
(Donot Add the script Nginx.conf)
14:Create directories to hold cache files
mkdir /usr/local/www
mkdir /usr/local/www/nginx_cache
mkdir /usr/local/www/nginx_cache/tmp
mkdir /usr/local/www/nginx_cache/files
chown www-data /usr/local/www/nginx_cache/files/ -Rf
15:create nginx.rb file
touch /etc/nginx/nginx.rb
chmod 755 /etc/nginx/nginx.rb
16:edit Nginx.rb
nano /etc/nginx/nginx.rb
(Add script Nginx.rb)
17:Install Ruby
apt-get install ruby
18:create cache dir
mkdir /cache1
chown proxy:proxy /cache1
chmod -R 777 /cache1
19:Start dir
squid -z
20:Start squid
service squid start
21:Restart Nginx
service nginx restart
22:Chek cached videos
ls -lh /usr/local/www/nginx_cache/files
23:chek cache hit
tail -f /var/log/squid/access.log | grep HIT
Credits:Syed Jahanzaib
Note:Copy One Line at a time
1:Create file
touch /etc/fw.sh
2:Change permissions
chmod +x /etc/fw.sh
3:Edit File
nano /etc/fw.sh
(Add the script simple internet sharing)
4:Run
/etc/fw.sh
5:Place shortcut
/etc/rc.local
6:Upgrade DNS
apt-get install dnsmasq
7:Update system
apt-get update
8:Install Squid
apt-get install squid
9:Edit squid.conf
nano /etc/squid/squid.conf
(Add the script squid.conf)
10:create storeurl.pl
touch /etc/squid/storeurl.pl
chmod +x /etc/squid/storeurl.pl
11:Edit store URL
nano /etc/squid/storeurl.pl
(Add store URL Script)
12:Install Nginx
apt-get install nginx
13:Edit Nginx.conf
nano /etc/nginx/nginx.conf
(Delete all lines in Nginx.conf)
(Donot Add the script Nginx.conf)
14:Create directories to hold cache files
mkdir /usr/local/www
mkdir /usr/local/www/nginx_cache
mkdir /usr/local/www/nginx_cache/tmp
mkdir /usr/local/www/nginx_cache/files
chown www-data /usr/local/www/nginx_cache/files/ -Rf
15:create nginx.rb file
touch /etc/nginx/nginx.rb
chmod 755 /etc/nginx/nginx.rb
16:edit Nginx.rb
nano /etc/nginx/nginx.rb
(Add script Nginx.rb)
17:Install Ruby
apt-get install ruby
18:create cache dir
mkdir /cache1
chown proxy:proxy /cache1
chmod -R 777 /cache1
19:Start dir
squid -z
20:Start squid
service squid start
21:Restart Nginx
service nginx restart
22:Chek cached videos
ls -lh /usr/local/www/nginx_cache/files
23:chek cache hit
tail -f /var/log/squid/access.log | grep HIT
Subscribe to:
Comments (Atom)